Security
Security is an important consideration of our application, so we must examine the chat application for potential vulnerabilities. Our design provides two access points to machines behind the server-side firewall:
- A port must be opened in the server-side firewall so that push clients can connect to the Glacier2 service. Clients connect to the firewall using an address defined by the firewall administrator; the firewall forwards these connections to the Glacier2 service.
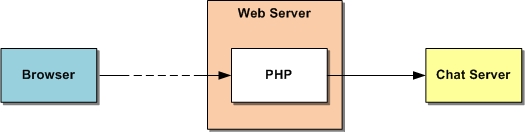
- Web clients communicate with a web server, which we assume runs behind the server-side firewall. Components running on the web server send Ice requests to the chat server on behalf of the clients.
Push Clients
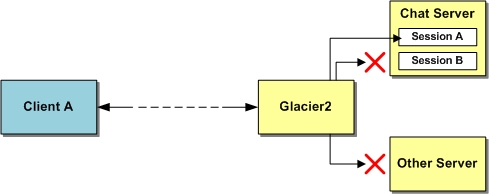
Glacier2 is a general-purpose request forwarding service that, by default, routes requests to any Ice object on any back-end host. Glacier2 also offers a number of security measures that applications can use to restrict the objects and IP addresses that are available to clients. The chat server employs these features so that the chat client is allowed to send requests only to its designated session object. Furthermore, the deployment runs Glacier2 and the chat server on the same host; therefore, Glacier2's configuration prevents chat clients from communicating with any other back-end host. The diagram below illustrates these restrictions:
One of our requirements is that traffic between clients and Glacier2 must be secure. This involves the use of a secure transport such as SSL or WSS.
Web Clients
The PHP chat client requires no special security precautions because, unlike Glacier2, it is not a generic request forwarder. Instead, the PHP client is simply an Ice program that happens to run inside the web server. There is no need for the client to obtain addressing information from the web user, which would carry significant risk. Because the PHP client runs behind the server-side firewall, the client can be configured with the address of the chat server and communicate with it directly.
One of our requirements is that traffic between clients and the server must be secure. In the case of our web-based clients, this involves the use of secure HTTP (HTTPS) between the browser and the web server. The PHP scripts could also use a secure transport when communicating with the chat server if they run on untrusted hosts.